-
Posts
3,134 -
Joined
-
Last visited
-
Days Won
494
Content Type
Profiles
Forums
Gallery
Downloads
Articles
Store
Blogs
Everything posted by datakick
-
I'm sure most of you know, and are using collectlogs module. If you are in need to update PHP versions of your store, this is very useful tool. It collects and report all deprecation warnings inside core/modules/themes that you need to fix before you can update to next PHP version. Once all warnings are fixed, it is very safe to update. I've very rarely experienced issues with update when all warnings were fixed before. I have recently updated php version for one store, but this time it went badly. The site displayed 500 after the update, and it took some time to get it working. I had to fix a lot of issues that should have been detected by collectlogs module, but weren't. Well, it turned out, that there was one module that was kind enough to turn off error reporting inside its constructor. So every time this module was used, all subsequent warnings were silently ignored. After update of PHP version, those warnings were no longer warnings but regular errors, and nobody can ignore that... I suggest you look into your modules main php files and look for error_reporting(-1); or error_reporting(0); It can looks like this: https://github.com/Hritani/matar/blob/9645ec14a0d8ca9fa2f7644b0b7b28c3f3bf76b4/modules/hooksmanager/hooksmanager.php#L8
- 1 reply
-
- 6
-

-

-

-
set Delivery delay (days) to 0/empty value
-
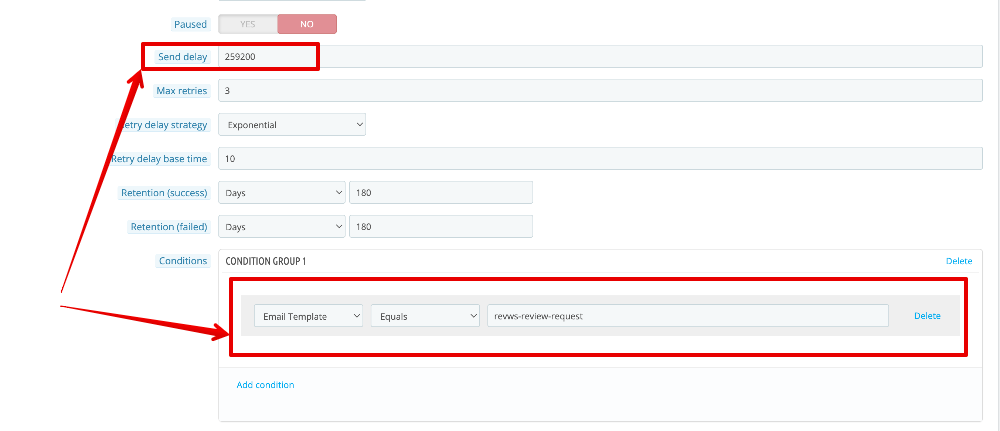
In revws, disable delivery delay completely, and send email based on order status only. Revws will send email immediately when the status changes, but emsil will be delayed by mailqueue
-
Since you have purchased mailqueue module, you can use it. Create a dedicated queue for revws review request email (condition = template = revws-review-request) and set send delay (in seconds) Note that revws review will show email as send, but it will wait in the queue before it's delivered.
-
I've just tested, and column delivery_date in order is set when order is set to status with 'Show delivery PDF' enabled. In your case, the column is empty -- this looks like some override or module changes the default behaviour. Or maybe there is some other process that updates the order record, and erases this column (webservice maybe?)
-
Is delivery slip generated for the order?
-
This is related to delivery_date field on order. This date is populated when order goes through status that generates delivery slip. Check your statuses configuration.
-
Revws module - possibly missing product structured data
datakick replied to 30knees's question in Module help
This is google being stupid, that's all. This warning is displayed when product doesn't have any reviews yet. We obviously can't write any metadata about review (author, content, rating) because none is written yet. We also can't write any metadata about aggregateRating - because what is the average of nothing? Allowed value for this field is in range of 1 to 5. If we used 0, then google would complain that this not a valid value we could put some value from the allowed range, but which? 1 -- that's not good, because then the page would be displayed with 1 star in search 5 -- that's better, but we would be lying -- nobody gave us 5 stars yet. And google could, and would penalize your site for that. The only solution here, in my opinion, is omit the information completely. -
This was introduced in 1.3.0
-
Display FAQ hook in different places when using multistore
datakick replied to the.rampage.rado's topic in FAQ Snippets
In smarty templates you can only use variables that were passed by controller. id_shop doesn't seems to be one of them You can call static methods from templates, though. You could add following line at the top of your template to declare this variable: {$id_shop = Context::getContext()->shop->id} And then use your original code (you don't need need isset() check anymore)- 1 reply
-
- 1
-

-
Did you correctly set the robots.txt when you installed the module ?
-
Who knows? You can test, and let us know. You can quite easily add lines with your custom smtp settings here: https://github.com/thirtybees/tbphpmailer/blob/08954acba40520d5d30e7514d122808ea9f04ec7/src/PhpMailerTransport.php#L103 For testing, there is no need for UI config in module settings page.
-
Add color label name to identify the atribute color
datakick replied to iceguitar's question in Technical help
This is not a simple customization where you can change one line and it will work. You need to look into your theme, find out relevant elements and attach onchange event listener to them. In event callback function you need to perform dom manipulation = figure out what colour is currently selected (see code above), and change the label of input group accordingly. If you are unsure how to do that, then you need to either study on the topic, or hire somebody to do that for you. -
Alternative, and maybe better, solution would be to move the message field from Address form to Carrier Selection form modify the override and save message during Carrier Selection form save
-
The address (second) step of this checkout flow contains two forms. form for address selection + message form for carrier selection The first form is never submitted -- the submit button was removed to facilitate this illusion of 3 steps. The address selection works because of attached ajax call to 'Choose a delivery address:' field. Message field, however, is not saved. To make this work, you need to: 1) add some onchange handler and submit message data to server. For example: <div id="ordermsg" class="form-group"> <label>{l s='If you would like to add a comment about your order, please write it in the field below.'}</label> <textarea class="form-control" cols="60" rows="2" name="message" id="message">{if isset($oldMessage)}{$oldMessage}{/if}</textarea> </div> <script> $('#message').on('change', () => { $.ajax({ type: 'POST', headers: { 'cache-control': 'no-cache' }, url: "{$link->getPageLink($back_order_page, true)|escape:'html':'UTF-8'}" + '?rand=' + new Date().getTime(), async: false, cache: false, dataType: 'json', data: 'ajax=true&method=updateMessage&message=' + encodeURIComponent($('#message').val()) + '&token=' + static_token, }); }); </script> 2) handle this ajax request on server. Modify the OrderController override that comes with this theme to look like this: public function initContent() { // save cart message if (Tools::isSubmit('ajax') && Tools::isSubmit('method') && Tools::getValue('method') === 'updateMessage') { $this->_updateMessage((string)Tools::getValue('message')); $this->ajaxDie(true); } parent::initContent(); switch ((int) $this->step) { case OrderController::STEP_ADDRESSES: $this->_assignCarrier(); //assigns carrier to address page step break; } }
-
Add color label name to identify the atribute color
datakick replied to iceguitar's question in Technical help
On product page you can function getCurrentCombinationAttributes and use it to find color name in javascript variable attributesCombinations Something like this: const selectedColorName = getCurrentCombinationAttributes() .map(id => attributesCombinations.find(obj => obj.id_attribute == id)) .filter(obj => obj.group === 'color') .map(obj => obj.attribute) .join(','); console.log(selectedColorName); -
Fonts / javascript loaded from external sources
datakick replied to DRMasterChief's topic in English
No, it's not. Neither core, nor niara/community-theme loads fonts from google apis in maintenance mode. It's your theme, or some module. -
Fonts / javascript loaded from external sources
datakick replied to DRMasterChief's topic in English
I've moved this discussion to separate thread, as it has not much to do with 1.5.1 release announcement 🙂 -
Chex module - customized product details display issue
datakick replied to x97wehner's question in Module help
Not easily, no. The product name displayed in checkout is supposed to be short text (not html), including customization data would make it very unreadable. -
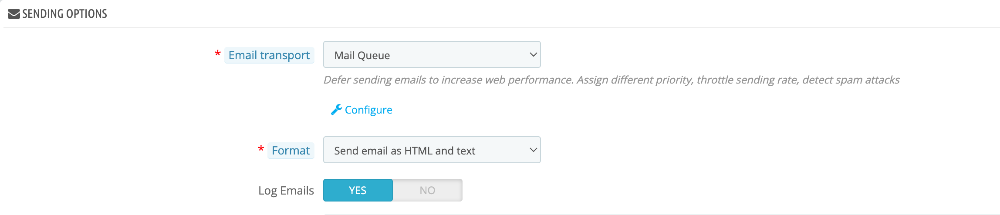
You have to set mailqueue as your default email transport in Email settings, otherwise the system will send it immediately.
-
Fonts / javascript loaded from external sources
datakick replied to DRMasterChief's topic in English
not thirty bees core / theme related -
That's true, chex does not have such functionality. Newest version of stripe let you sort stripe payment methods, so that can help.
-
Which flag makes the order status to restock the items?
datakick replied to the.rampage.rado's question in Technical help
I'm afraid none. As far as I know, there's hardcoded logic for PS_OS_CANCELED and PS_OS_ERROR statuses, and that's it. https://github.com/thirtybees/thirtybees/blob/6c9db328c27a93be59b7ed8d32cef8deb0169105/classes/order/OrderHistory.php#L174-L217 -
There is some (probably module/override) code that access this property on front-office controllers. You have to figure out what code is that, and fix it -- it should probably work with back-office controllers only. Look at stacktrace for this error to figure out what code attempts to access the property.
-
First line should look like this: public function &__get($name)