-
Posts
3,134 -
Joined
-
Last visited
-
Days Won
494
Content Type
Profiles
Forums
Gallery
Downloads
Articles
Store
Blogs
Everything posted by datakick
-
I've added this to backlog
-
There are technical limitations for what can be tracked. This module can track only direct object model properties, and only if that object is saved using object model add() / update() / save() method. So properties like price, default category, reference code, enabled, description, ean, sale flag etc can be tracked. Basically this means columns from tb_product / tb_product_shop / tb_product_lang tables. Associations (relationships between tables) such as categories, tags, carries, etc can't be tracked this ways. That's because there is no hook triggered when relationships changes. There isn't even any unified way in tb core to change associations. Similarly, if something is changed using direct db update, then such change will not be audited.
-
History module is a very simple module that provide audit functionality for your products and categories. Did you ever wonder why, when, or who changed your product description or price? This module will provide answer for these questions.
-
Shortcodes is a premium module for thirty bees supporters that let you use shortcodes in your product description. Currently, you can use HTML within descriptions. This is very often used to create link to other products, categories, or pages within your site. Over time, these hardcoded links can stop working properly (for example if you change rewrite, or move product to different category). Shortcodes offers solution for this problem. Instead of creating link to product, you can simply add shortcode like [product id=34] link [/product] And thirty bees will automatically generate correct link for you. Moreover, the link will use to current context -- if you are browsing your site in french language, the links will also point to french products. The same applies to multi-store context. Module also contains (optional) functionality to automatically convert HTML links to shortcodes. So if you, or your employee, enter HTML link to some product, module will detect it and replace the <a href="https://www.domain.com/en/category/product.html">link</a> with [product id=34] link [/product] shortcode. Module will also report all internal links that it could not be converted -- so you can go and fix them manually. Supported shortcodes: At the moment, only a few shortcodes exists. We plan to implement many more. And not only for linking content. We can use shortcodes to embed more interesting stuff, for example review ratings, product cover image, or what have you. If you have any ideas, let us know! [product id=id] - creates hyperlink to product. Optional parameters: shop, language [product_url id=id] - generates url string for product. Optional parameters: shop, language [category id=id] - creates hyperlink to category. Optional parameters: shop, language [category_url id=id] - generates url string for category. Optional parameters: shop, language [cms id=id] - creates hyperlink to cms page. Optional parameters: shop, language [cms_url id=id] - generates url string for cms page. Optional parameters: shop, language Roadmap: support shortcodes in more contents -- currently, you can use shortcodes only in product short and long descriptions. In the future, we want to add support for other rich contents (category descriptions, cms pages, blogposts,...) support for custom shortcodes registered by modules. Modules (for example beesblog) will be able to register shortcodes that you can use to embed module content, for example link to blog post [blogpost id=100] link [/blogpost] more friendly parameters, so you won't have to use internal ids. For example to generate link to product in fr context, you could write [product id=1 language=fr] instead of [product id=1 language=3]
- 1 reply
-
- 3
-

-

-
missing swiftmailer causing issues in modules since TB 1.5 update
datakick replied to smarterweb's question in Technical help
Note that this dirty fix is not the best and long term solution. Better would be to modify the mail.php file and remove dependency on specific implementation of email transport. -
missing swiftmailer causing issues in modules since TB 1.5 update
datakick replied to smarterweb's question in Technical help
That's unfortunate. This module depends on library that is no longer provided by core. The dirty fix could probably be to install tbswiftmailer module, and then edit this modules/awocoupon/helper/mail.php file, and include library from tbswiftmailer module. require_once(__DIR__ . '/../../tbswiftmailer/vendor/autoload.php'); -
ThirtyBees 1.5 OFFICIAL is here!
datakick replied to the.rampage.rado's topic in Announcements about thirty bees
Yes, this is the reason. Core updater offers only versions supported by your PHP version, and 1.5.0 is not supported on PHP7.2. I suggest you update your store to thirty bees 1.4 (if you are not on that version yet) update to PHP 7.4 check that everything works -- core should work nicely, but some modules can have issues. update your store to thirty bees 1.5 install collectlogs module, and start collecting all warnings and deprecations (these will come mostly from modules) wait few days and let collectlogs do it works fix critical issues in modules (you can ask on forum which issues are critical and which not) update your php to 8.0 again wait and collect (new) warnings related to PHP8.0 if no critical issues exists, you can safely update to PHP8.1 do the same for PHP8.2 It's a long process, but it's safe when done properly. -
ThirtyBees 1.5 OFFICIAL is here!
datakick replied to the.rampage.rado's topic in Announcements about thirty bees
Thanks for reporting this, I'll investigate. I haven't encounter any issue myself with it, though. Yes, this is not supported yet. For this to work, we need to implement single-sign on across all our services (api, store, forum, www, accounts....) and synchronize user identity across them. That's a big project. We have it on our back log, but it's not highest priority. Once we have single user identity, we can offer downloading premium modules from store. Until then, we just don't know if store customer is member or not. -
Modules page displays local modules (modules present locally in /modules/ directory) modules available through thirtybees api I guess we could (and should) add a filter to hide non-local modules
-
Thank you. I've picked your changes and released new version of module.
-
Why can a new customer group still see products when they cannot see categories?
datakick replied to Obi's question in Technical help
Works (somewhat) properly for me, I've just tested it with homefeatures and blockbestsales modules. The logic for product availability is complicated. Every product can belong to multiple categories. Customer can belong to multiple groups. To be order-able, product must be associated with at least one category that is associated with at least one customer group -
Nice one, this should be part of the module. You can create pull request here, and we'll merge it: https://github.com/thirtybees/mailalerts
-
That's great, I love that the collectlogs module help fixing bugs in third party modules. The prestabay module probably pass $product->link_rewrite directly to Link::getImageLink method. Depending on mode the $product object was instantiated, this property can either contain text, or array of texts (one for each language). I guess in this case it's the later. This would result in image url like https://domain.com/1-Niara_home/array.jpg instead of expected https://domain.com/1-Niara_home/product-link-rewrite.jpg It is not a big deal, because both urls are valid. But the first url is ugly, wrong, and not-so-much SEO friendly.
-
Easy Change of Product Listing from 3 Column to 4 Column
datakick replied to Obi's question in Theme help
near miss. It's in file /themes/{{theme}}/product-list.tpl How to change it depends on theme -- every theme can implement this differently. Some paid themes can have this configurable, some not. In default theme (niara, community-theme-default) this is not configurable. Number of columns depends on the class used for individual product block -- smarty variable product_block_size_class. There is already some logic that switches between different number of columns depending on page name: https://github.com/thirtybees/niara/blob/d469fcb47b589783deebe847b77bc8d1c0a1d242/product-list.tpl#L3-L6- 1 reply
-
- 1
-

-
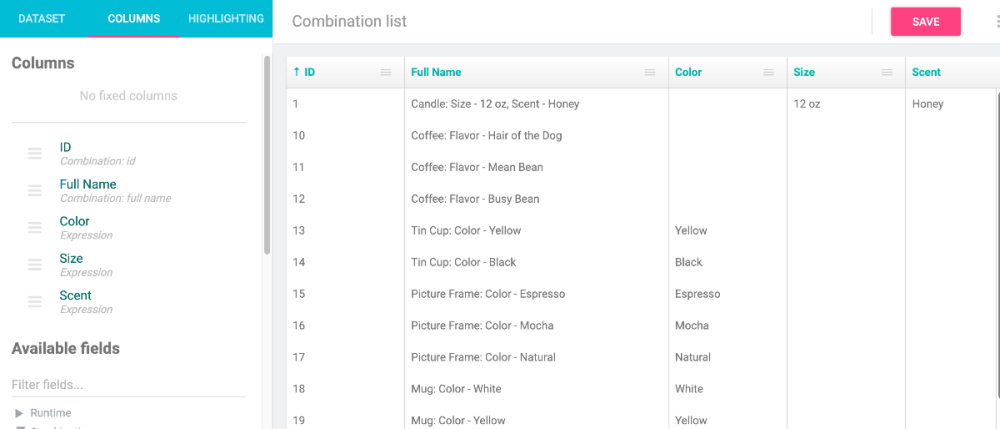
Congrats, you have discovered a bug 🙂 This will be fixed in next release. Meanwhile, you can edit file modules/datakick/engine/prestashop/functions/combination-attribute-value.php and change lines 97 and 88 from AND comb.id_product_attribute = ' . (int)$combinationId . ' AND a.id_attribute_group = ' . (int)$attribute . ' to AND comb.id_product_attribute = ' . $combinationId . ' AND a.id_attribute_group = ' . $attribute . ' With the fix in place, you can extract any attribute value, if you know attribute group id. For example, if I have these attributes groups: I can create list of combination, and use combination id + constant 3 to extract color from combination: combinationAttributeValue(combinations.id, 3)
-
Migrate Prestashop to a new thirtybees installation
datakick replied to haylau's question in Technical help
You can edit file psonesixmigrator/classes/ConfigurationTest.php and change line 322 to true. https://github.com/thirtybees/psonesixmigrator/blob/bcc9d1d12fb5e47b6a613a6ecebdf9b6fed1ab05/classes/ConfigurationTest.php#L322 public static function testFopen() { return true; } -
a lot of php encryption and blowfish encryption warnings
datakick replied to Beeta's question in Bug Reports
Yes, that is the problem. You have (for some reason) set your store to use PHP Encryption, but no encryption key is generated. No idea how this happened. Because no encryption key exists, thirty bees will raise the first warning: "PHP Encryption can't be used because _PHP_ENCRYPTION_KEY_ constant is not defined." And fallback to Blowfish encryption. Blowfish encryption is deprecated, and raises the second warning. The fix is very simple. Go to Performance tab switch encryption to Blowfish. Save switch encryption to PHP Encryption Save That's it. When you change encryption from Blowfish to PHP Encryption, system will generate new encryption key if none exists. -
Multistore - change navbar-header color for specific store
datakick replied to Beeta's question in Theme help
I've just pushed this to bleeding edge. Your body tag will now have class depending on selected context, for example mulstistore-context-all, multistore-context-group-1 or multistore-context-shop-2 You can add custom css into <admin_dir>/themes/default/css/overrides.css body.multistore-context-shop-3 .bootstrap #header_infos { background-color: lightgreen; } -
That makes sense. Thanks for investigating, I've pushed the fix to bleeding edge.
-
{if !$priceDisplay}{convertPrice price=$product.price}{else}{convertPrice price=$product.price_tax_exc}{/if} replace with simple {$product.price} On a related note -- I strongly recommend to remove all rich snippets markup metadata from this file. Imagine you have product page that shows 9 related products in the footer. When google parses this page, it sees that this page contains information about 10 products. Which is not true - the page contains one product, and 9 links to related products. Similarly, when google index your category page, it sees that this is page that contains 12 products. Again, that's not true. It is category listing page with links to 12 products. Having product metadata in product miniature blocks creates unnecessary noise which can confuse search engines. Just get rid of them, and google will be able to better index your pages.
-
I don't have this issue. Do you have some reprosteps?