-
Posts
3,122 -
Joined
-
Last visited
-
Days Won
488
Content Type
Profiles
Forums
Gallery
Downloads
Articles
Store
Blogs
Everything posted by datakick
-
Neither community theme, nor niara theme, supports tabs on product page. It's not hard to do, but I guess the theme author liked all-in-page better then tabbed content
-
That's theme responsibility. Some themes render tabs as a normal sections with headers
-
That is correct. Current situation regarding PHP 7.4 is very similar to the one we had year ago regarding PHP 7.2. It works just fine, the only problem is that there is a lot of notices in error log. You can turn these off or ignore them, of course. Or wait until they get fixed. Hopefully they will.
-
Thanks for reporting this issue. This is my fault - I've copied / pasted the uninstall method from my other module, and it does not work in this one. Anyway, the fix is very simple -- delete the uninstall method completely (lines 47-50). And then try to uninstall again.
-
You probably have some variable that can't be serialized to string, and exception is throws when trying to do so. Look into your logs (both server and in thirtybees/logs directory), might shed some light on it. Also, you can modify themes/debug.tpl template and remove following line to prove this is the root cause: <td>{$vars|debug_print_var nofilter}</td>
-
I would advice against this. There may be other code in the theme, or javascript, that depends on this option. If you set this to false, you are basically saying that your store does not use stock management at all (which is not true, I believe, otherwise you would turn this off in back office settings page). This can cause you a lot of weird bugs in the future. Since you are already modifying the template, you can simply delete the code that displays this 'in-stock' information. Alternatively, if you want this to be 'configurable', you can introduce your own variable, like {assing var='SHOW_IN_STOCK_INFO' value=false} and then update already existing condition in the template to include this new variable.
-
This doesn't look like ps16 theme, it's probably ps17 theme. Correct? If so, then you can't use it on thirtybees. Prestashop 17 modules / themes are not compatible
-
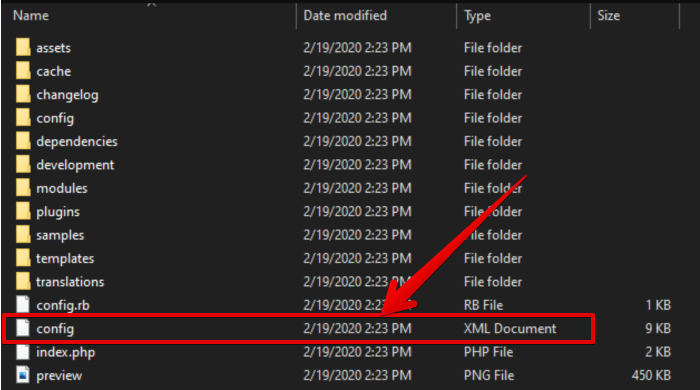
Could you attach config.xml from the zip file?
-
First of all, you should update your thirtybees to bleeding edge using core updater. It will give you better error message, at least. Anyway, to your question -- thirtybees failed to load config.xml file from the zip file. The file either doesn't exists, or it is not a valid xml file. You should examine zip file to see it's content. Sometimes, zip file distributed by theme developers contains another zip file (the actual theme archive) and few other files, like installation manual or documentation.
-
Yes, the css for block cart is specific for blockTop position, it's not possible to just move it to displayNav without modifying css and/or associated js. But it's possible. You noted that you have the first problem solved, so I'll just comment on the second problem. Change the #layer_cart css rule to this #layer_cart { background-color: #fff; position: fixed; top: calc(50vh - 250px) !important; left: 8%; display: none; z-index: 99; width: 84%; } That might help. Of course, adjust according to your needs
-
I don't know what that mean, root overrides. The only location that thirtybees loads overrides from is <root>/override/... Does the file <root>/override/controllers/front/ContactController.php contain the lines above? If so, then the module should work. Unless you have disabled overrides in your back office performance settings. Another common reasons why overrides don't work is old file cache/class_index.php In this file, thirtybees track information about all installed overrides files. Sometimes, this file get out of sync with reality (especially when you edit overrides manually)
-
This module uses optional overrides, which means override is not installed during module installation. Instead, it's installed on demand when you toggle on the Contact form button in module settings. The resulting override file should contain these lines
-
If you have this override already installed, then installation of override from nocaptcharecaptcha will fail. That's because both overrides target the same method, and it's not possible to automatically merge the code. The good news (for tb developers at least) is that the module works correctly. The bad news is that it should report the failure of override installation -- that should be fixed.
-
Looks ok. Please check the override. On a totally unrelated note -- the image upload functionality should work again in the forum. Could you please check and confirm?
-
also, check that the ContactController override is installed.
-
I'm sorry, but this is impossible to understand 🙂 At least for me. Could you please re-phrase it?
-
You didn't get the idea of a multistore at all. Multistore means that you have only one installation that handles all your stores. These stores can have different domains associated, you just need them to point to the same IP address you thirtybees is running on. When visitors visits any one of these stores, thirtybees will determine the correct shop context from the url, and will serve content from that shop only. Of course, you can decide if your mutli-stores will share products, customers, orders, etc. You can set it as you wish. The main benefit of multistore is that you can manage everything from one back office
-
Waiting will not help. It should / must work when you open url in browser. The blank page itself is ok, that's an expected behaviour. But the exchange rate should be updated. Look into your error logs (both server and in thirtybees /log directory) to see if there's any clue why. If there's nothing, the only think you can do is debug.
-
What does it mean? Do you get 404 / 500 http response? Some error in error log? The currency cron script don't output anything, it's a blank screen. This is intentional, and not a bug.